In a highly digitized society, digital identity is more important than one’s physical identity. The irony is that today we do not own our digital identity and our digital identities are held by trust corporations and third parties. Digital identity and decentralized identity are two different approaches to managing a person’s digital identity.
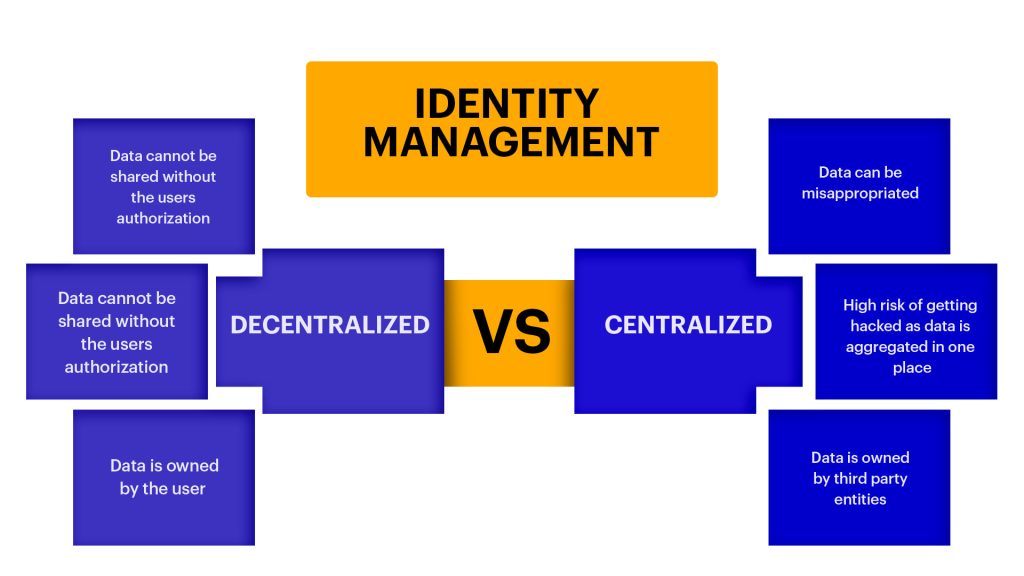
A digital identity is a traditional approach to identity management that relies on centralized authorities, such as governments or businesses, to store and manage a person’s identity information. This information is typically stored in a database, and a person must provide their credentials, such as a username and password, to access it.
Decentralized identity is a newer approach to identity management that gives individuals more control over their identity information. In a decentralized identity system, a person’s identity information is stored in a distributed ledger, such as a blockchain, and individuals have the ability to control who has access to their information.
As shown by recent events, there have been multiple data breaches exposing the personal information of millions of people.
Decentralized identity solutions have been created to level the current playing field in an attempt to regain control of our identities in the digital space.
What is Decentralized Identity?
Decentralized identity, also known as Self-Sovereign Identity, is a digital identity model that allows for the custody of one’s own digital identity without the need for a third party. This model is not only limited to individuals and can be used by organizations, devices, and other entities. 1
Our digital identity consists of usernames, passwords, search history, birthdate, social security number, purchase history, etc.… by allowing the self-custody of such data, individuals can control who has access to them and provide only the information that is required to be verified.
Decentralized identity is built upon three pillars,
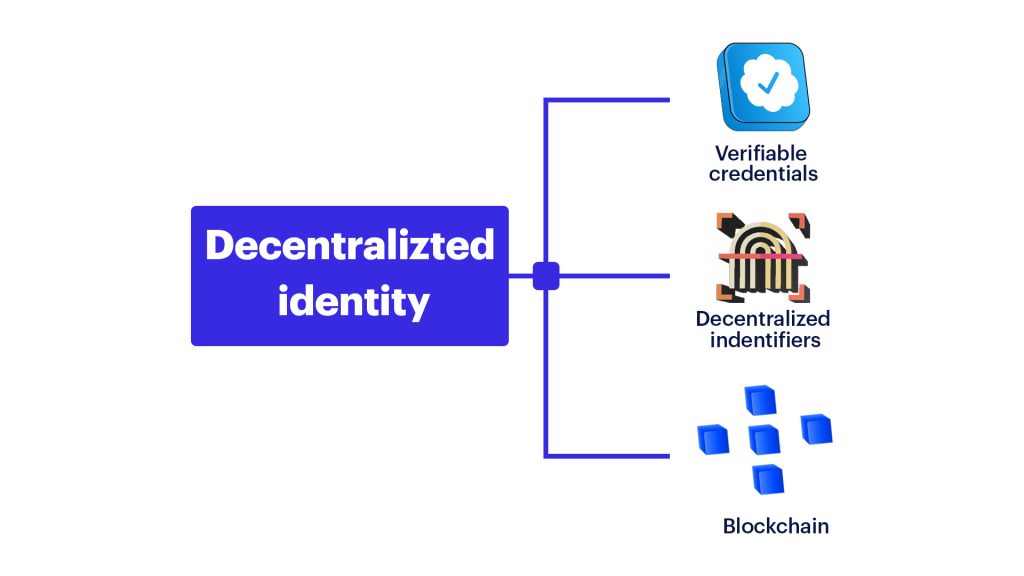
- Verifiable credentials (VCs) – Verifiable credentials are digital representations of a claim or piece of information that can be independently verified by a trusted third party. They can be used to securely share information, such as qualifications, licenses, or certificates.
- Decentralized identifiers (DIDs) – Decentralized Identifiers are a type of digital identifier that allows individuals, organizations, and devices to have a unique and verifiable online identity without the presence of a centralized entity. 2
- Blockchain – Blockchain is a distributed ledger technology that allows for secure, transparent, and tamper-proof record-keeping. It uses cryptography to secure the data and is maintained by a network of nodes rather than a centralized entity.
With decentralized identity, users can collect the above-mentioned verifiable credentials about themselves from certified users and provide them to requesting parties, which in turn verifies the data with ease.
How does it work?
Similar to cryptocurrencies, digital identities also use encrypted blockchain-based wallets. Users are able to store their verifiable credentials and generate decentralized identifiers through the wallet application. This approach is safer than storing digital credentials with multiple third parties, as digital wallets are protected with encryption and a distributed architecture.
These wallets can be installed on mobile phones and are identifiable on the blockchain through their public keys, while the private keys are used to provide authentication. With this approach, decentralized identity wallets transparently authenticate while protecting user data.3
Benefits of Decentralized Identity
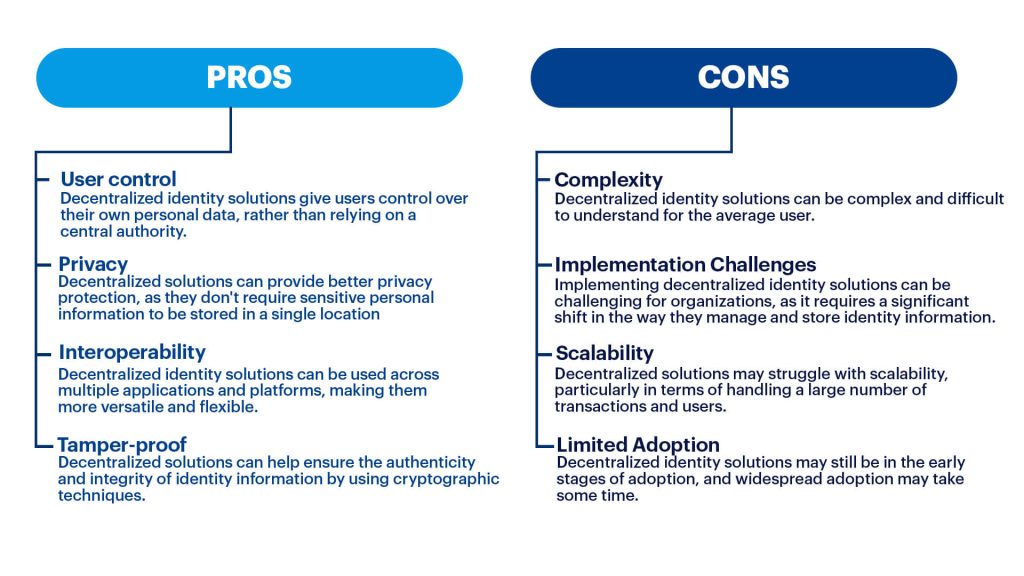
For individuals, decentralized identity provides many benefits, such as ownership and control over one’s own personal information, enhanced privacy, and greater convenience, as the same identity can be used to access different services without making new accounts.
The benefits associated with it are not only limited to individuals, but they extend to businesses as well. Let us look at a few of these benefits below,
- Efficiency: Organisations are able to reduce the time associated with processes, such as hiring, by streamlining the verification process.
- Reduced cost: By not having to store user data, businesses can cut down on data storage-related costs.
- Trust: Decentralized identity systems provide a more secure and trustworthy way of verifying identity, reducing the risk of fraud and identity theft.
- Improved security: Through the use of cryptography and encryption, sensitive data is secured.
- Interoperability: Decentralized identity systems can allow for easier interoperability between different services and systems.
Risks and Challenges
Decentralized identity solutions, while offering numerous benefits, also present various risks and challenges. One of the main technical risks is the possibility of bugs and vulnerabilities in the code that could be exploited by malicious actors. Additionally, the concept of decentralized identity is still new to many people, and there may be challenges in terms of widespread adoption and understanding.
Another challenge is the lack of standardization in the decentralized identity space, leading to potential compatibility issues between different solutions. There are also concerns about privacy and security, as personal information is being stored and managed in a decentralized manner.
In terms of regulation, there is currently a lack of clear guidelines and regulations for decentralized identity solutions, which can create uncertainty and difficulties in their implementation.
Pros & Cons of Decentralized Identity Solutions
In today’s landscape, verifiable proof of existence is essential to exercise our right as citizens to access services such as healthcare, banking, and education.
According to various surveys, more than 1 billion people in the world do not have official proof of identity and are barred or restricted from the services mentioned above. Decentralized identity systems can help to reduce this number as only an internet connection is required for access. Further, as the world shifts from WEB2 to WEB3, traditional forms of identification will not be sufficient.
Overall, while decentralized identity solutions have the potential to revolutionize the way we manage and control personal information, this technology is still in its infancy, and it is important to weigh the benefits with its associated risks and challenges.
- Techopedia “techopedia.com“[↩]
- 101 blockchains “101blockchains.com.“[↩]
- Decentralized identity management vs centralized identity management – dock.io “dock.io“[↩]


