Introduction
You may have heard about cryptocurrencies such as Bitcoin and Ethereum, but have you ever wondered where your cryptocurrency is stored? We have bank accounts to store credit or debit transactions of fiat money. Like that, do we have anything for cryptocurrency? Yes, they are called crypto wallets. Some may say we have stored our cryptocurrencies on exchanges, not wallets. Still, when we investigate this deeply, all exchanges manage their users’ wallets on your behalf. In this article, you’ll learn about what a crypto wallet is, the types of wallets, the reasons to have them, how to keep them securely, and how to choose one based on your needs.
What is a Wallet?
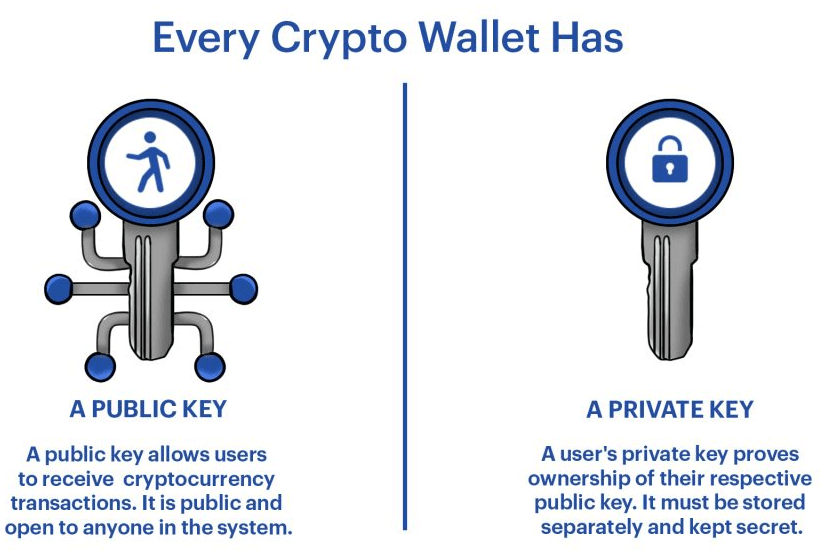
First, you must understand the fundamental difference between traditional and crypto wallets. In traditional wallets, we store cash and cards inside the wallet, but in crypto wallets, we don’t store the coins or tokens themselves; those are always livelily available on the blockchain; what we hold are the private keys and reference to the assets. A private key is similar to an ATM PIN used to authorize transactions; just like an ATM PIN, we’re not supposed to share it with anyone else. The public key, on the other hand, can be shared, and it is used to generate the wallet address, which is the equivalent of an account number.
In simple terms, a crypto wallet is a tool to securely store our cryptocurrency and NFTs keys and prove that you are the owner of a particular crypto address or account when interacting with a blockchain network. In addition, you can use crypto wallets to authorize transactions when sending or receiving crypto assets.
Reasons to have Wallets and Who needs them
If you are going to invest in cryptocurrencies or purchase a portion of Bitcoin, you will need a crypto wallet first. You can also use them to make transactions between peers. If you decide to go with a centralized exchange like Binance or Coinbase, they will give you access to a wallet to store your cryptocurrency. These crypto wallets serve a wide range of use cases. For example, with your wallets, you can access blockchain networks. You may have heard about dApps. They require a wallet to prove that you are the owner of the wallet address used to sign into the dApp. In some countries, such as EL Salvador, the government regulated cryptocurrencies, resulting in many retailers and e-commerce companies accepting cryptocurrencies as payment. As a result, citizens of EL Salvador must have a Crypto Wallet to pay for their services and products. Unlike the traditional banking system, not all crypto wallets are custodial. Instead, there is a range of varieties, and according to their use cases, they can be divided into multiple categories.
Types of Wallets
As noted above, different wallet options serve different purposes. First, they can be defined as “Hot” or “Cold” according to their operation. Then, according to the private key accessible scenario, they can be categorized as Custodial and Non-Custodial. For the more technical folks among you, they can be classified further as deterministic and non-deterministic according to the way private keys are generated.
Let’s look at them one by one.
- Hot Wallets
These are referred to as hot wallets because they are often used in immediate use cases. In addition, they are always connected to the internet, easy to set up, and easily accessible. These things make it a comfier option for frequent users and day traders. Hot wallets contain the private keys of the wallet inside the application itself. Even if they’re stored in an encrypted way, the networks they are connected to may have vulnerabilities. If you have a lumpsum amount of crypto in a hot wallet, it’s always seen as bad practice. We recommend using cold wallets in those scenarios. Web-based wallets like browser extensions, Mobile Wallets, and Desktop Wallets are a few examples of hot wallets.- Mobile wallets: Mobile wallets are simple apps that can be found on the Play Store and App Store. They allow you to make transactions on the go. But they carry an additional risk that your mobile phone could be stolen or get lost. E.g., Trust Wallet, Atomic Wallet, Metamask mobile.
- Desktop Wallets: Just like mobile wallets are mobile apps, desktop wallets are computer software. Examples include Bitcoin-QT and Brave wallets.
- Browser extensions: E.g., Metamask, Yoroi, etc.
- Cold Wallets
Unlike hot wallets, cold wallets are kept offline. They use a physical tool to store things; you can’t make any transactions with these cold wallets alone. This device must be connected to another device via a USB with an internet connection, or the user must type the private keys stored in it into another device. This makes cold wallets inconvenient for frequent users but drastically increases security. Even if a cold wallet was stolen, the thief would be unable to do anything without knowing the wallet password or seed phrase. Cold wallets are always the HODLs’ and long-term investors’ cup of tea. Paper wallets and Hardware wallets are examples of cold wallets. - Custodial Wallets
Most of the wallets offered by cryptocurrency exchanges are custodial wallets. Custodial means that the private keys needed to make a transaction will be kept under control by the exchange. In this scenario, users will trust the crypto exchanges to completely control their assets. - Non-Custodial Wallets
Non-custodial wallet providers let users gain complete control over their assets, and the private keys are stored locally with the user. That’s why when creating a non-custodial wallet, users are prompted to save randomly generated words known as a “seed phrase.”
Security of Digital Wallets
Imagine you are buying cryptocurrency from a peer. In that situation, the sender (the peer) needs to know your wallet address to send the assets. After you’ve received the amount, you need to sign the transaction with the private key to spend those cryptocurrencies, verifying that you are the wallet owner. When creating a new wallet, a message will likely prompt you to write down a list of 12 to 24 random words. It’s called a “Seed Phrase,” a mnemonic phrase. It helps to reduce human errors in backups. Even if you lose access to your wallet, keys, or the device you had wallets in, you can simply restore them with the seed phrases n number of times. However, please remember that if you can restore the wallets with a seed phrase, someone else can. So, don’t disclose seed phrases to anyone. Using a wallet within an exchange is always advised to protect your account with Two two-factor authentication (2FA). Other wallet users should keep their private keys in a secret place. Don’t store them on your note app, or don’t screenshot them and save them to your cloud drive. It is considered best practice to write it down on a piece of paper and store it in a secure place. If you’re a HODLer, a cold wallet is recommended.
Closing Thoughts
Now you may have understood what wallets are, their use case, types of wallets, and why you should never disclose your private keys or seed phrases to someone. Each wallet type has both advantages and disadvantages, and you should choose one based on your needs and risk tolerance.


