Table of Content
Zero Knowledge Proof (ZKP) is a ground-breaking idea in the fields of cybersecurity and cryptography that enables one party to demonstrate to another that a statement is true without disclosing any information beyond the statement’s veracity. The complexities of ZKP, its usage in the financial sector, and its revolutionary effects will all be covered in this blog.
What is Zero Knowledge Proof?
A cryptographic technique known as “Zero Knowledge Proof” allows one party (the prover) to demonstrate to another (the verifier) that they are aware of a value or piece of information without actually sharing any information other than their knowledge.
For example, imagine you want to prove to a friend that you know the password to a safe without revealing the password itself. You can do this by entering the password and opening the safe in a way that your friend can see the safe opens but cannot see the password you entered. This is a simple analogy for Zero Knowledge Proof (ZKP).
How Does Zero Knowledge Proof Work?
To fully appreciate ZKP’s (ZKP) potential, one must comprehend how it operates. Therefore, let’s go over the fundamental ideas, investigate the various kinds of ZKPs, and talk about some of the most often utilized algorithms in real-world applications in this section.
Key Properties
- Completeness: If the statement is true, the honest verifier will be convinced by the honest prover.
- Soundness: If the statement is false, no cheating prover can convince the honest verifier that it is true.
- Zero-Knowledge: If the statement is true, the verifier learns nothing beyond the fact that the statement is true.
Types of Zero Knowledge Proof
ZKPs can be broadly categorized into two types:
- Interactive Proofs
- Non-Interactive Proofs
Each type has its own use cases and advantages.
Interactive Proofs
To verify a statement’s validity, the prover and verifier communicate back and forth via interactive proofs. The prover answers a series of questions from the verifier in a way that persuades the verifier without disclosing the secret.
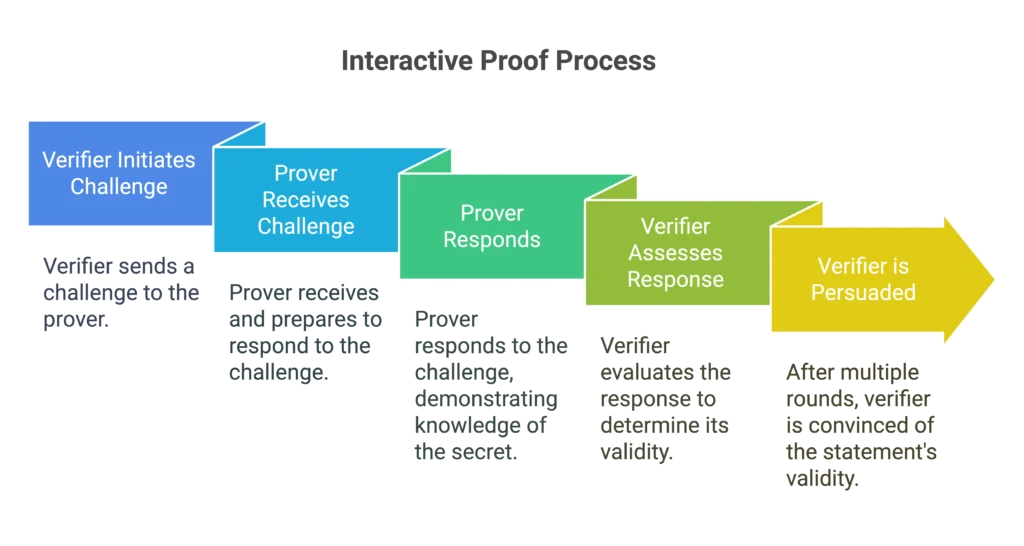
How It Works:
- Several message rounds are exchanged between the prover and verifier.
- The prover receives arbitrary challenges from the verifier.
- Each challenge is answered by the prover in a way that shows they are aware of the secret.
- The verifier is persuaded of the statement’s veracity after multiple rounds.
For example, consider a cave where two entrances (A and B) are connected by a hidden door that can only be opened by the prover. Standing outside, the verifier requests that the prover leave through either A or B. The prover has a 50% probability of making the right guess if they don’t know the secret, but they can always comply if they do. The likelihood of cheating is almost eliminated when this procedure is repeated several times.
Non-Interactive Proofs
There is no need for back-and-forth communication with non-interactive proofs. Rather, a single evidence is produced by the prover, which the verifier can independently verify. This improves the scalability and efficiency of non-interactive proofs, particularly for blockchain applications.
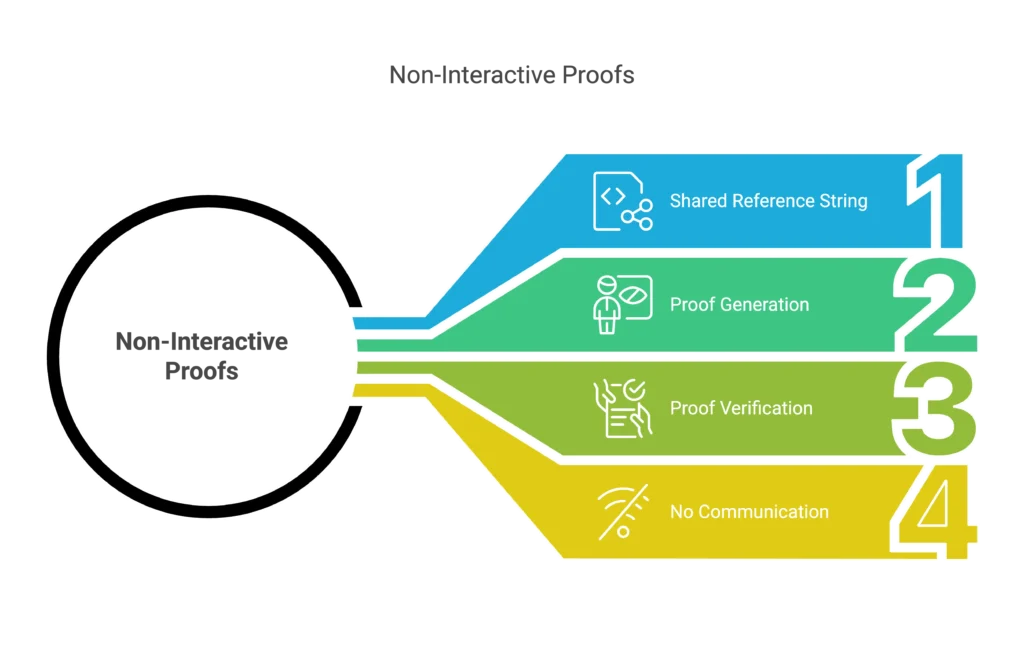
How It Works:
- A shared reference string (a public parameter) is used by the prover to produce a proof.
- The same reference string is used by the verifier to compare the proof.
- No more communication is required.
Blockchain systems frequently use non-interactive proofs. For example, Zcash facilitates private transactions through the use of zk-SNARKs, a kind of non-interactive proof. Without disclosing the sender, recipient, or transaction amount, the sender creates evidence that the transaction is legitimate.
How Does Zero Knowledge Proof Help the Financial Sector?
- Enhanced Privacy
Privacy is crucial in the finance industry. Financial organizations can confirm transactions and customer identities with ZKP without disclosing private information. ZKP, for instance, can be used by banks to verify that a client has enough money for a transaction without disclosing the precise amount in their account.
- Reduced Fraud
By enabling private and secure verification procedures, ZKP can drastically lower fraud. To reduce the danger of identity theft and data breaches, credit card firms, for example, can employ ZKP to confirm that a transaction is authentic without disclosing the cardholder’s information.
- Improved Efficiency
Conventional financial procedures can need a lot of paperwork and several middlemen. By facilitating safe and effective verification, ZKP can expedite these procedures. ZKP, for instance, can be used by blockchain-based financial systems to confirm transactions without requiring third-party verification, which lowers transaction costs and delays.
What are the Common Algorithms in Zero Knowledge Proof?
Advanced cryptographic techniques are necessary for Zero-Knowledge Proofs to operate effectively and safely. Over time, researchers have created a number of methods to apply ZKPs in practical settings. Today, zk-SNARKs and zk-STARKs are two of the most popular techniques; they are both made to strike a balance between scalability, security, and efficiency.
Let’s first examine the necessity of these algorithms before getting into the details. Let’s say you wish to demonstrate to someone that you have figured out a difficult puzzle without giving away the answer. You need a strategy that will persuade people fast (efficiency), guarantee that they can’t figure out a solution on their own (security), and be scalable enough to solve even the biggest problems. In cryptographic systems, zk-SNARKs and zk-STARKs accomplish exactly this.
zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge)
Zk-SNARKs are a potent technique that enables one side to support a claim with little exchange of information. They are frequently employed in applications that improve privacy, especially in blockchain networks.
Why Does It Matter?
- Extremely succinct—proofs are small and quick to verify.
- Requires a trusted setup, a predefined cryptographic process that must remain uncompromised.
- Used in privacy-focused cryptocurrencies like Zcash.
Zk-SNARKs are used by Zcash to facilitate private transactions. Without disclosing the sender, recipient, or quantity, a user can demonstrate that they have enough money and are conducting a legitimate transaction.
zk-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge)
A more recent advancement that enhances zk-SNARKs by eliminating the requirement for a trusted setup and providing better scalability is zk-STARKs.
Why Does It Matter?
- No trusted setup: removes the security threats related to the creation of starting parameters.
- Scalable: manages big calculations effectively, which makes it perfect for Layer 2 blockchain scalability.
- Post-quantum security: impervious to future quantum computer threats.
Zk-STARKs are used by StarkWare, the company behind StarkNet, to increase Ethereum’s scalability. Zk-STARKs allow for quicker and less expensive transactions without sacrificing security by combining thousands of transactions into a single proof.
zk-SNARKs VS zk-STARKs
| Feature | zk-SNARKs | zk-STARKs |
| Setup | Requires a trusted setup | No trusted setup required |
| Proof Size | Small | Larger than zk-SNARKs |
| Verification Speed | Very fast | Slightly slower than zk-SNARKs |
| Quantum Resistance | Not quantum-resistant | Quantum-resistant |
| Use Cases | Zcash, Ethereum zk-Rollups | Scalable blockchain solutions |
In contemporary systems, especially those in blockchain and finance, zk-SNARKs and zk-STARKs are essential for providing anonymity and scalability. They open the door for innovations like decentralized finance (DeFi) and private smart contracts by enabling the safe, private, and effective verification of transactions and calculations.
Challenges and Limitations of Zero Knowledge Proof
- Computational Complexity: ZKPs can be computationally demanding, involving a large amount of time and computing power. This may prevent them from being widely used, particularly in real-time applications.
- Scalability Issues: The difficulty of creating and validating ZKPs may create a bottleneck as transaction volume rises. Scalability for ZKP-based systems is still a major problem.
- Regulatory Concerns: ZKP’s privacy characteristics may cause regulatory issues, especially in the banking industry where transparency is frequently necessary to stop money laundering and other illegal activity. One of the main challenges is striking a balance between privacy and regulatory compliance.
Future of Zero Knowledge Proof
Zero-Knowledge Proofs (ZKP) have already revolutionized financial transactions, blockchain, and authentication in terms of security and privacy. However, ZKPs are anticipated to get even more potent as technology advances. Here are the four main ways that ZKP will influence the future:
Integration with AI:
The need for privacy in AI models has grown as artificial intelligence (AI) becomes more widespread. Large datasets are frequently needed by AI systems. However, sharing private information presents moral and security issues. An innovative way to enable AI models to learn from data without disclosing it is to integrate ZKP with AI.
Possible Usage:
- Secure Federated Learning: AI models can be trained collaboratively by several entities (banks, hospitals, etc.) while maintaining the privacy of their data. ZKPs make it possible to confirm that the model was correctly trained without disclosing specific data points.
- Bias-Free AI Auditing: AI systems can demonstrate that they adhere to moral and equitable principles without disclosing sensitive data or secret training techniques.
- Verifiable AI Predictions: Without disclosing the internal decision-making process, AI-generated outputs (such as fraud detection and credit rating) can be shown to be based on reliable calculations.
Quantum Resistance:
Even though ZKPs now provide robust cryptographic security, conventional cryptographic techniques are in danger due to the development of quantum computing. The development of quantum-resistant ZKP algorithms is essential since popular encryption systems could be cracked by quantum computers.
Possible Usage:
- Since zk-STARKs rely on hash functions rather than number-theoretic assumptions, they already provide post-quantum security.
- Lattice-based ZKPs, which take advantage of mathematical structures that are difficult for quantum computers to decipher, are being developed by researchers.
- To guarantee long-term security, hybrid cryptographic approaches that combine classical and quantum-resistant techniques are being investigated.
Wide Adoption of Financial Services:
ZKP-based privacy solutions are becoming more popular among banks, payment processors, and decentralized finance (DeFi) platforms as the financial sector undergoes a digital revolution. ZKP use in financial services is anticipated to rise sharply as regulations change and consumer demand for financial privacy rises.
Possible Usage:
- Confidential Transactions: ZKPs can be used by banks and payment networks to validate transactions without disclosing private information such as counterparties or amounts.
- Regulatory Compliance with Privacy: Without disclosing user data, ZKPs can help banks demonstrate adherence to Know Your Customer (KYC) and anti-money laundering (AML) laws.
- Improvements to DeFi Privacy: ZKPs can be used by lending protocols and decentralized exchanges (DEXs) to validate transactions without compromising transparency.
- Central Bank Digital Currencies (CBDCs): Governments are investigating ZKPs to develop digital currencies that provide transactions that are auditable while maintaining anonymity.
Interoperability:
ZKP needs to be smoothly integrated across many platforms, blockchains, and authentication systems in order to be widely adopted. ZKP-based solutions may communicate efficiently without being restricted to separate ecosystems because of interoperability.
Possible Usage:
- ZKP Protocols Across Blockchains: ZKP-powered bridges are being developed by projects like zkBridge to validate transactions across several blockchains without the need for centralized middlemen.
- Standardized Frameworks for ZKP: Industry-wide initiatives to standardize ZKP implementations across smart contracts include Ethereum’s EIP-4337.
- Interoperable Identity Verification: ZKPs can facilitate decentralized identity (DID) systems, which let users authenticate themselves across various services without disclosing private data.
ZKPs are a strong cryptographic tool with many uses, especially in the financial industry. By increasing efficiency, decreasing fraud, and boosting privacy, ZKP has the potential to completely transform the way that financial transactions are carried out. To reach its full potential, though, issues including scalability, computing complexity, and regulatory constraints need to be resolved. ZKP is positioned to be a key component of safe and private online transactions in the future as technology develops further.


