Table of Content
- Understanding Blockchain networks and Decentralization
- What can be achieved through 51% attacks?
- The consequences and potential damages of 51% attack
- Networks that faced 51% attacks
- How expensive is it to conduct a 51% attack?
- Is an attack on BTC a possibility these days?
- Which networks are at risk?
- Indications that a network may be prone to 51% attacks
- Steps to be taken to prevent 51% attacks
- Conclusion
Blockchain is the underlying technology behind cryptocurrencies. Unfortunately, as this technology evolves, people are developing new ways to misuse and perform malicious actions. The 51% attack or a majority attack is one of them, which refers to a situation in which a miner or a group of miners gain control of more than 50% of the computing power on a blockchain network.
What would happen if they took control of it like this? First, it implies that the miner who performed the attack will have most of the mining power and can perform mining faster than others already in the network.
So, then what will be the consequence? It’s almost like the shareholders of a traditional company, who own more than half of the shares and start to influence important decisions. Likewise, in the blockchain network, they can execute several malicious activities, such as reversing transactions, double-spending, and preventing new transactions from being confirmed.
We have just looked at the theoretical possibilities until now. Next, let’s dive into the feasibility of this attack, past events in history, why the Bitcoin network is secure, and more.
Understanding Blockchain networks and Decentralization
Before continuing deep into 51% attacks, it is crucial to have a good understanding of the fundamentals of blockchain. One of the key aspects of a blockchain-based system is its distributed and transparent nature. It operates on a network of computers called nodes, where each node maintains a copy of the ledger. The ledger is updated through a consensus mechanism, where transactions are verified and confirmed by the nodes on the network.
This ensures that the ledger is a tamper-proof record of all transactions on the network. However, most nodes need to reach a consensus regularly regarding the validity, process, etc.
Consensus algorithms are a mechanism that allows users to coordinate in a decentralized setting. For example, proof of Work and Proof of Stake are types of consensus algorithms.
Bitcoin for example is based on PoW, meaning miners must contribute computational power and broadcast the block hash to the rest of the network. The miner only gets rewarded for adding a new block to the network; once the network nodes collectively agree on the block hash, the miner broadcasts, Regardless of whether the network participants are 100 or 1 million. If most of the participants validate the block hash, then the algorithm will agree with the collective decision.
What can be achieved through 51% attacks?

As you know, a distributed network of nodes will maintain the transactions occurring in the network, and miners will verify them and earn their reward. There is no room for a single entity or monopoly. If a malicious actor wants to gain a monopoly, they must possess enough mining power. There is no limit to what they can achieve by gaining monopoly power. Some common scenarios are:
- Reversing transaction:
The attacker could potentially reverse the transaction record that has already been confirmed by the network. - Double spending:
In this type of attack, an attacker attempts to spend the same cryptocurrency twice by reversing one of the transactions. This is done by creating two conflicting transactions, with one transaction being confirmed by the attacker’s mining power while the other is discarded by the network. This means that the attacker will retain the currency they have already spent. - Block censorship:
This means that the attacker can selectively approach new blocks and potentially exclude transactions from being processed. - Selfish mining:
Block other miners from mining coins or tokens within the network.
The consequences and potential damages of 51% attack

The “majority attack” is not a common occurrence, but it is important to consider the repercussions of falling victim to such an attack. If a network is subject to an attack, it will lose credibility, community trust, and at least some monetary value. Furthermore, a domino effect will follow.
- New transactions will be delayed.
- Causes network disruption or Denial-of-Service.
- Reduced miner rewards.
The good news is that there are some limitations to what malicious actors can do. For example, they cannot:
- Reverse transactions made by other people
- Alter the number of coins or tokens generated by a block
- Create new coins or tokens from nothing
- Transact with coins or tokens that don’t belong to them
As a blockchain grows, it becomes more difficult for rogue miners to attack it; however, smaller networks are more vulnerable, as the participants and hash rate are lower compared to Bitcoin.
Networks that faced 51% attacks
- Bitcoin Gold – In 2018, Bitcoin Gold (BTG), a cryptocurrency based on Bitcoin, suffered its first attack, resulting in the theft of $18 million from cryptocurrency exchanges. In 2020, it suffered another attack.
- Ethereum Classic – Suffered two attacks in 2019 and 2020, and in both instances, attackers managed to double-spend ETC coins. The second attack cost the network $5 million worth of ETC.
- Vertcoin – Experienced multiple attacks.
- Grin – The attacker gained 57% of the hashing power and intruded.
- Expanse – A go-Ethereum clone experienced an attack in July 2019.
- Litecoin Cash – a Bitcoin Core clone, faced multiple attempts to carry out a major attack, but the attackers ultimately only managed to double-spend a small amount of money.
How expensive is it to conduct a 51% attack?
Now, you have an idea about these attacks and how challenging and difficult they are. To gain a better understanding, let’s look at some mining pools and ASICs that have higher hash rates.
The top five mining pools by hash rate are,
- Foundry USA – 37.06%
- AntPool – 16.55%
- F2Pool – 14.22%
- ViaBTC – 10.26%
- Binance Pool – 9.79%
So, as per our theories and all, we must merge the Foundry pool and Antpool to generate a whopping 148.66 EH/s (around 1.4866 million TH/s) to gain 53% of the hash rate share.
The bitmain ASIC S19 XP Hydro has a hash rate of 250 TH/s 1 and was priced at USD 19,000 last year. So, the economic feasibility of performing such an attack is very low.
Also, remember that major cryptocurrencies and large networks with many participants are not the targets of attackers due to the exorbitant costs of acquiring that much hashing power. Thus, small blockchain networks of altcoins are the attackers’ targets.
Even after Ethereum’s transition towards Proof-of-Stake, an attack on the Ethereum network became more and more expensive since if you want to perform a 51% attack, you probably need to stake 51% of ETH. That’s around 6.9 million Ethereum, worth more than 9 billion USD.
In addition to an immense amount of hashing power, timing, and luck also play a significant role when performing an attack, as the mining process is random. Even if the attackers attained 51% of the hashing power of a particular network, they might not be able to keep up with the block creation rate or get their chain inserted before valid new block hashes are generated and broadcast by the legitimate network participants.
Is an attack on BTC a possibility these days?
No, the cost of acquiring the hashing power alone can prevent it from happening. By February 2023, attackers will need to control more than hundreds of hashes per second of EH/s of hashing power in order to gain control.
Which networks are at risk?
It’s probably hard to say since it depends on many things. One key theoretical aspect is that you can win if you have enough mining power. Blockchain networks which can be mined with GPUs are more vulnerable than ASIC (Application Specific Integrated Circuits) secured networks.
Sometimes, the attackers don’t have to spend time buying hardware. Instead, they can just rent out cloud services and make the attack happen against the GPU-only networks.
Further, the Michigan Institute for Technology has built a system to actively monitor scores of PoW networks and detect chain reorganizations, known as “reorgs,” 2 which can act as an indicator for attacks. That system can also estimate the attack’s cost based on the hash rate rental prices at the time of the attack.
Since they launched that system in 2019, the system has detected 40 reorgs 3 on coins such as BTG, VTC, EXP, and LCC. Obviously, they all were smaller cryptocurrencies at that time based on the hash rate, and they were GPU-specific networks. So, attackers easily performed the attacks by renting out cloud services.
Overall, as an investor or as a user, keep in mind that no blockchain networks are immune to attacks.
Indications that a network may be prone to 51% attacks
Before investing in any cryptocurrency or before using a blockchain network for transactional purposes, it is important to research the network and make sure that the network is secure and safe. Here are some steps you can follow to determine if they are vulnerable.
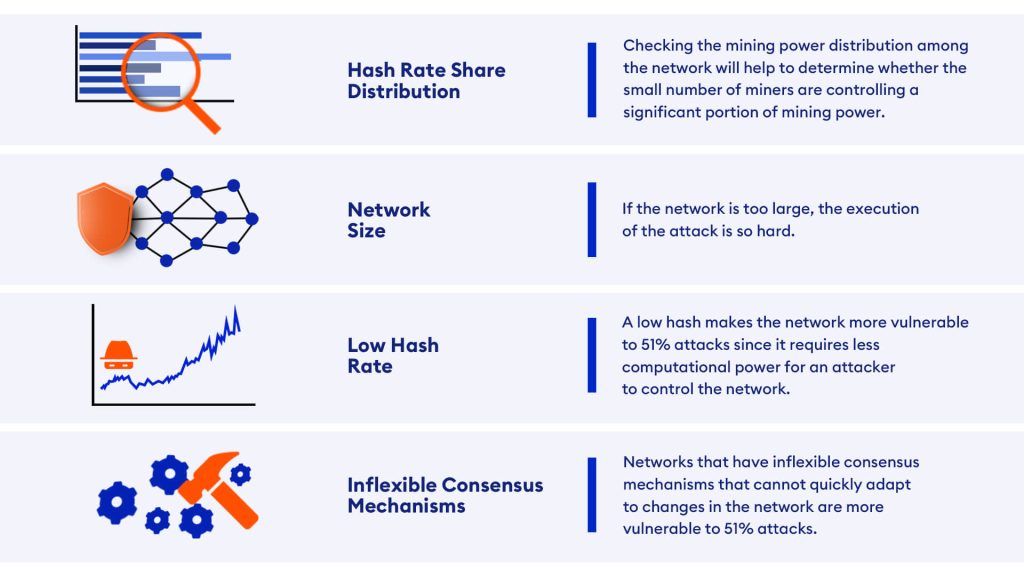
Steps to be taken to prevent 51% attacks
The Digital Currency Initiative (DCI) of MIT’s system tracker is in action to find reorgs. Other than that, these are some ways to lower the potential occurrences of 51% of attacks.
- 50% limit on a single miner
Blockchain developers must ensure that no one controls more than 50% of the hashing power. - Using PoS instead of PoW
All PoW blockchain networks have terms that the miners must regularly upgrade their equipment as difficulty hikes. Refusing these terms may end up not getting block rewards and falling behind the other miners inside the network, leading to a centralization of mining power. - Strong network community
When using PoS or DPoS (Delegated proof of stake), a user with a minimal stake level in a network is voted a block validator. The validators are voted in by the community. In case of collusion to compromise the network, the community throws them out.
Conclusion
Cryptocurrency investing may appeal to investors comfortable with taking more risks to pursue higher returns. If an investor is new to cryptocurrency trading, the prospect of a 51% attack might seem intimidating. Understanding how they work and the likelihood of one occurring can help them assess the risks of their investments.
As a developing technology, we must embrace the benefits as well as the shortcomings and work towards resolving these issues to promote decentralization. But, at the end of the day, it’s helpful to be aware of the security measures and take steps in order to secure our coins from 51% attacks.
- Bitmain ASIC: https://www.bitmain.com/[↩]
- MIT’s new system, named as reorgs : https://dci.mit.edu/51-attacks[↩]
- MIT’s newly built system: https://dci.mit.edu/51-attacks[↩]