Table of Content
The need for privacy is increasing. People are worried about their personal data being exposed and getting hacked. This is worrisome for many because it could risk their jobs, titles, and even lives. The risks that come with a lack of privacy should not be taken lightly. Without privacy, individuals may find themselves exposed to unwarranted surveillance and scrutiny, which can impact their personal and professional lives. In addition, the loss of privacy can lead to identity theft, cyberbullying, and other forms of online harassment. It can also limit freedom of expression and lead to self-censorship, as individuals may feel inhibited from sharing their thoughts and ideas. The Zero Knowledge Proofs Protocols are inherently private and secure. The only information that is revealed in a ZKP protocol is whether or not the prover knows a certain secret. This means you can confidently share sensitive information with those who need it without fear of it being leaked to the public or used in any malicious way against you.
What is a Zero Knowledge Proof?
ZKP is basically an encryption protocol that takes place between two ends. One end will be the prover, and the other will act as a verifier. When this protocol is taking place, the prover can convince the verifier that they know about a certain secret without revealing the contents of the secret. In simple terms, proving the validity of a statement without revealing the message.
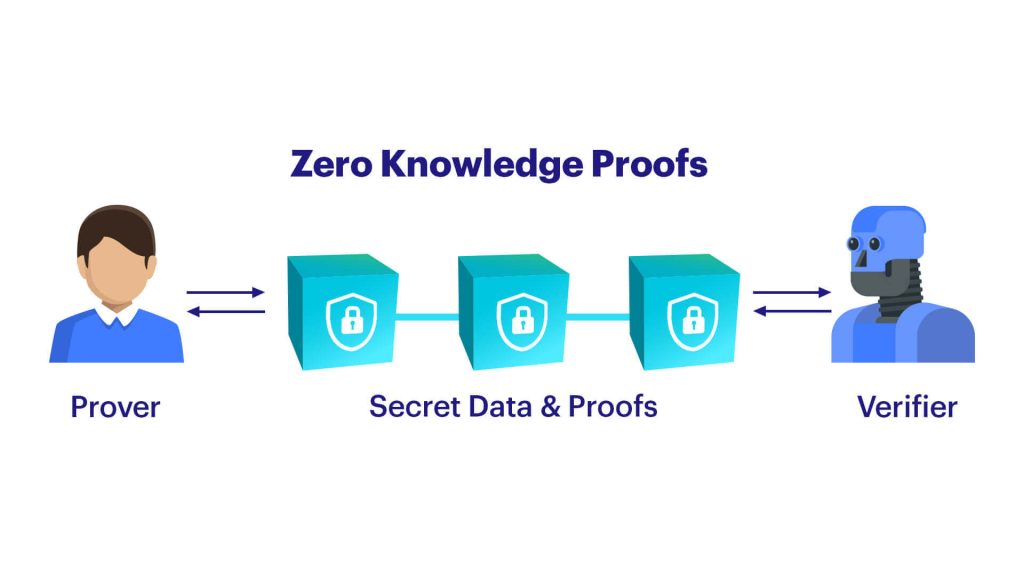
That secret information can be anything, such as solutions for a mathematical problem or even a complex security question. It’s like trying to figure out the place someone has visited recently. You may throw them a bunch of questions about that place which, if they answer correctly, prove that they’ve been to that particular place. The more questions they answer correctly, the higher the probability they actually visit there. Moreover, They don’t have to give you the names of the people they visited in that nation. And you’re not required to inquire. So it doesn’t affect the transaction. Hence sensitive information is safeguarded in this way.
The well-known Ali Baba cave story by Jean-Jacques Quisquater1 is a fantastic example of how interactive proofs operate. In the tale, Peggy, the prover, seeks to convince Victor, the verifier, that she knows the code necessary to open a magic door without disclosing the wording. Currently, a website requests the user’s password as input before comparing its hash to the previously stored one, similar to a bank that depends on your credit score to approve your loan. In this system, the host servers are in charge of your information, and there is always a risk of data leakage. However, if ZKP is used, the login can still be validated even when the client’s password is unknown to the verifier, reducing your exposure to threats.
How do Zero Knowledge Proofs enhance blockchain?
Now you may have questions regarding why ZKP is needed with blockchains; first, you need to understand the nature of the transactions on the blockchain. When a transaction takes place, anyone can monitor the wallet addresses of the sender and receiver, as blockchain is built on a distributed ledger system where each party can have a copy of the records. Still, there is no direct link between a wallet address and a specific entity or person, as wallet addresses do not require a KYC (Know Your Customer); hence it is challenging to link transactions on the blockchain to anyone.
We encounter certain transactions where it is essential to prove our identity, and this can be done by providing official documents such as Identity cards and driving licenses. Using ZKP, we can verify our identity without the documents mentioned above, ultimately proving our identity while maintaining privacy.
Diving into the technical aspects, a ZKP must satisfy three properties,
- Completeness,
- Soundness
- Zero-Knowledge
Completeness means that if the statement is valid and both the prover and verifier are honest, the prover will convince the verifier of the message’s validity. Soundness will ensure(with a high probability) that if the statement is false, a dishonest prover will not be able to convince an honest verifier that it is true. Finally, zero knowledge conveys that the verifier won’t learn anything beyond the prover’s validity, and the contents of the statement are safeguarded.
Pros and Cons of Zero Knowledge Proof
Now let’s take a quick look at the pros and cons of this protocol. The first advantage is simplicity since it doesn’t require complicated encryption protocols. Privacy and robust security can increase blockchain throughput, and finally, it has the perfect combination of privacy and scalability.
If we look at the negatives, hardware costs and inefficiencies are the main drawbacks since ZKP contains thousands of calculations that require a certain amount of time to process. Additionally, costs are required to verify proofs, and the proof message might be lost or corrupted in transit. Another limitation is that a ZKP protocol only provides probabilistic evidence, not a deterministic one, even though the margin of error can be reduced to insignificant levels. Finally, the risks associated with quantum computing are also another drawback.
Final thoughts
In this era, where we are witnessing so many rapid technological innovations, blockchain has shown us and continues to show us the absolute benefits of decentralization, transparency, and immutability. Combining ZKP with blockchain technology will provide an additional layer of privacy for transactions enhancing blockchain utility. ZKP was first coined in an MIT paper published by Silvio Micali and Shafi Goldwasser in 1985: “The knowledge complexity of interactive proof systems.” 2 This paper defines this Zero knowledge is widely used today, and the rest is history.
- Alibaba cave story by Jean-Jacques from one of his research papers itself: https://pages.cs.wisc.edu/~mkowalcz/628.pdf[↩]
- people.csail: https://people.csail.mit.edu[↩]